Recently, the SK Telecom SIM hacking incident has warned of the risk of digital ID theft, going beyond mere personal information leakage. Once the communication network collapses, all services connected to banks, public institutions, portals, and social networks could fall into the hands of attackers in an instant.
SIM (Subscriber Identity Module) plays a crucial role as it stores the identification number (IMSI) and subscriber authentication key (Ki) of a mobile communication device. In Korea, phone number-based personal identification is widely used in financial transactions, public petitions, and various authentication procedures, making the SIM card serve as a digital identity card.
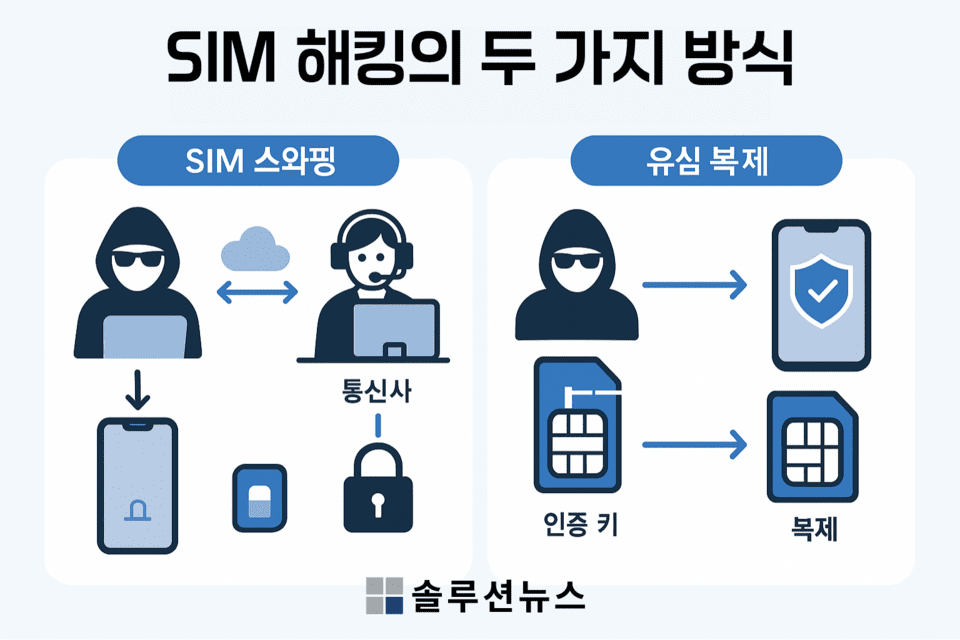
SIM hacking occurs in two ways. One is ‘SIM Swapping’. The attacker first gathers the victim’s personal information to approach the telecom company, disguising themselves as the victim and requesting a reissue of the SIM. If the telecom company conducts a lax identity verification process, the attacker gains complete control over the victim’s phone number. The stolen number is then used to bypass two-factor authentication for banks, messengers, and email accounts, and reset passwords. The victim is expelled from the network, while the hacker, impersonating the victim, gains access to all information.
The other method is SIM cloning. Hackers exploit system vulnerabilities to steal the authentication key (Ki) stored in the original SIM and replicate this information onto a cloned SIM. The cloned SIM possesses the same authority as the original. Telecom companies perceive both SIMs as belonging to the same user, allowing the hacker with the cloned SIM to intercept all communications and authentication processes.
A significant issue is that most two-factor authentication relies on SMS text messages. If a SIM is stolen or cloned, the hacker receives the verification text as well. Transfer approvals, password reset notifications, and new login alerts all fall into the hacker’s control. The victim might even take a while to notice as they won’t receive any texts.
This risk is especially deadly for individual users relying on weak multi-factor authentication systems. As the trust model based on existing communication networks breaks down, the digital trust framework in society might also become unstable.
In response to this situation, SK Telecom is offering free SIM replacements at over 2,600 T World stores nationwide and recommending enrollment in the ‘SIM Protection Service’. The SIM Protection Service includes an additional identity verification process during SIM changes to prevent illegal alterations.
Security experts argue that SIM protection alone is insufficient. They advise transitioning from SMS-based verification to OTP (One-Time Password) and urge financial institutions and messaging apps to use separate security apps. Furthermore, telecom companies are emphasized to strengthen non-face-to-face SIM reissue processes and enforce the adoption of biometric or multi-factor authentication methods.
This incident starkly reveals how much Korea’s authentication system depends on a single communication network. As intrinsic vulnerabilities in the personal information verification system are uncovered, the possibility of similar damage expanding in the future is raised.